tags: devops tool ansible,devops,tools,ansible,tutorial,2019,ansible add remote hosts in inventory,add remote hosts,ansible remote host authentication method,automation tools,ansible_ssh_pass,ansible authentication using ssh key,ansible authentication with password,linuxtopic,linux topic,ansible hosts,ansible video turorial,ansible tower,ansible documentation,ansible family,ansble open source,
Ansible
OS - CentOS 7
Kernel - 3.10.0-693.17.1.el7.x86_64
IP - 172.17.20.100
Hostname - linuxtopic.com
Remote Nodes:
Node 1 :
UefiPXE = 172.17.20.98
Node 2 :
Video Tutorial in Hindi

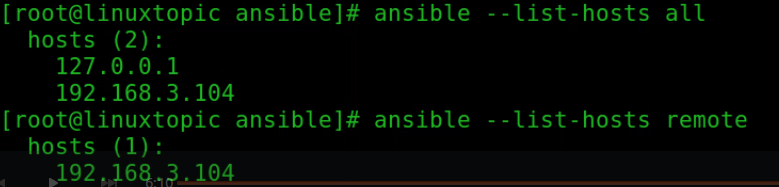
To check all configure hosts
2) Authentication ansible hosts using ssh key
Prepare ssh key in remote hosts, for example we have Ubuntu 16 with details:
Remote Host: 192.168.3.104
User: lokesh
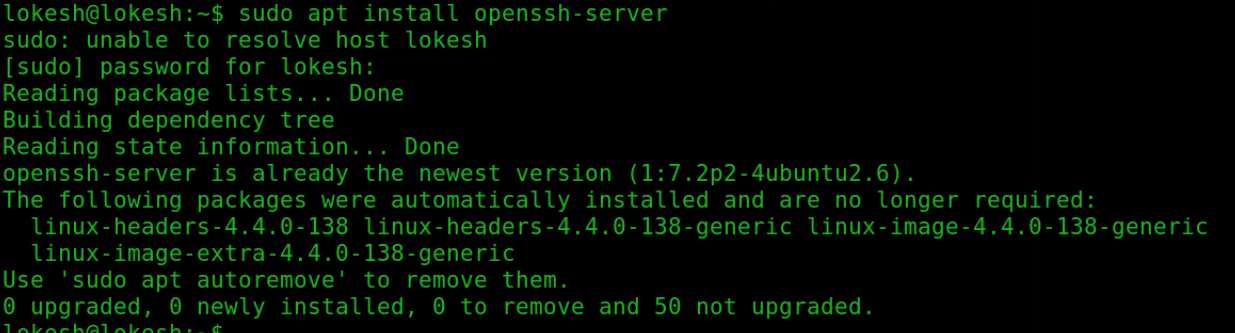
To Install Openssh-server in Remote host
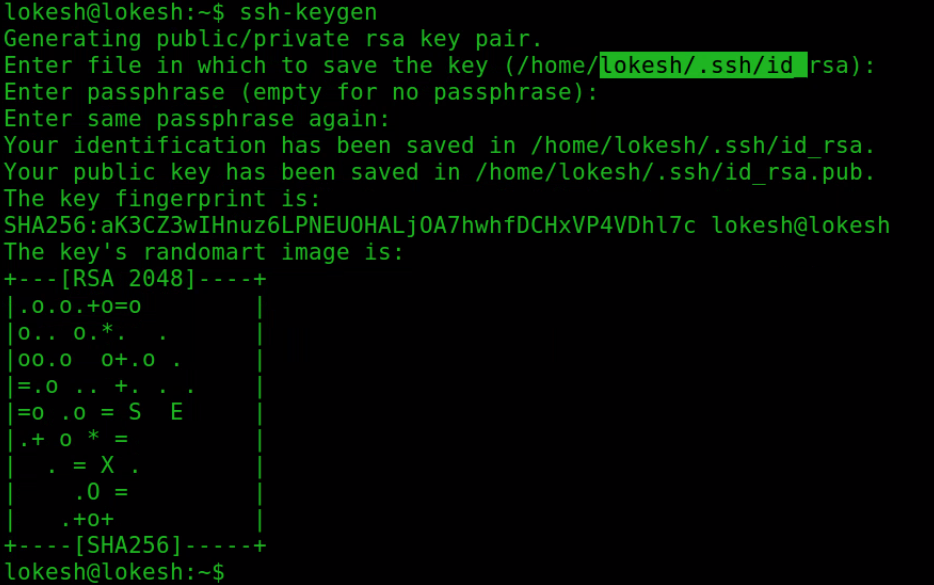
To generate ssh key using ssh-keygen
To verify ssh key file

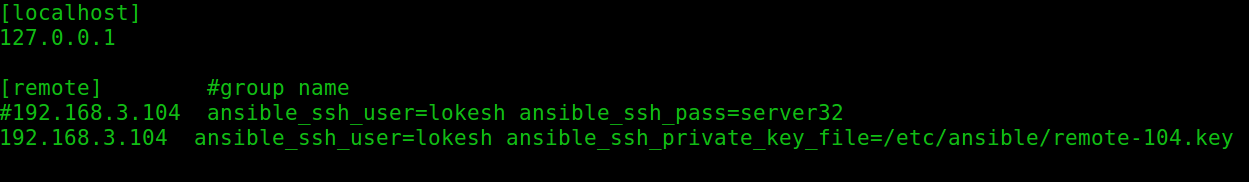
Add remote host in inventory file using key file path
127.0.0.1
[remote]
192.168.3.104 ansible_ssh_user=lokesh ansible_ssh_private_key_file=/etc/ansible/remote-104.key
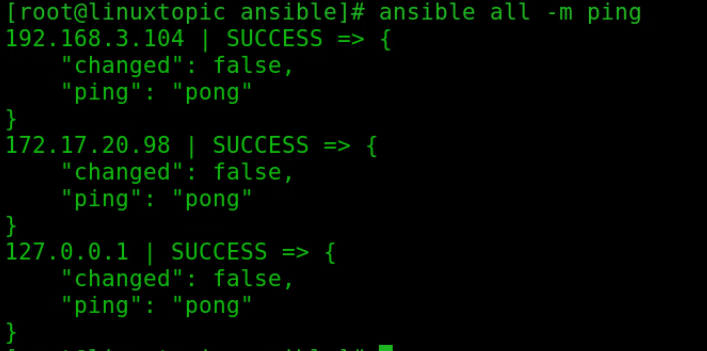
Verify hosts connectivity using ping module

3) ssh-copy-id
To copy ssh key using ssh-copy-id command
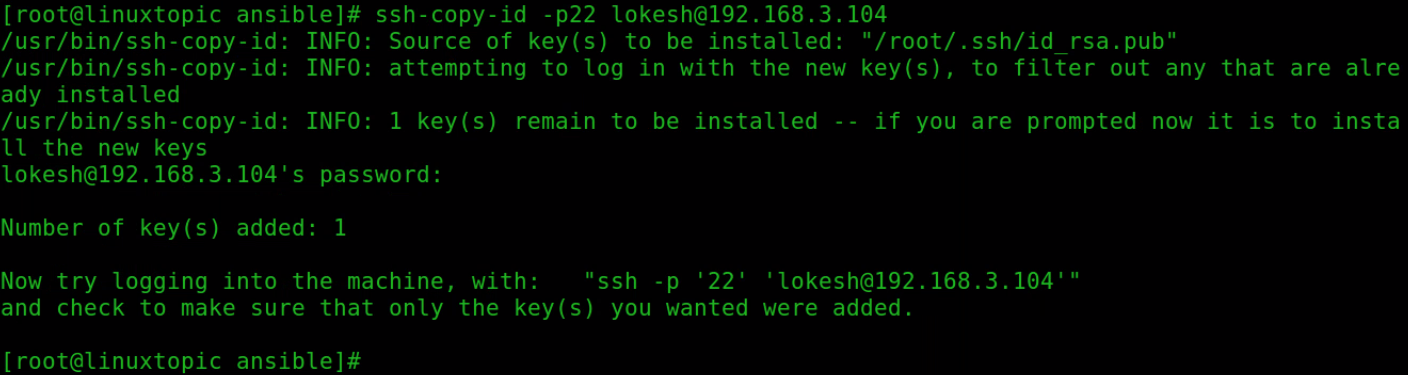
Here: ssh-copy-id is command, -p22 is ssh port, lokesh is ssh user and 192.168.3.104 remote host
Host 2:

127.0.0.1
[remote]
192.168.3.104 ansible_ssh_user=lokesh ansible_become_pass=server32
172.17.20.98 ansible_port=22022

In inventory we use ansible_become_pass=server32, means we give sudo privileges
To verify all hosts using ping ad-hoc command
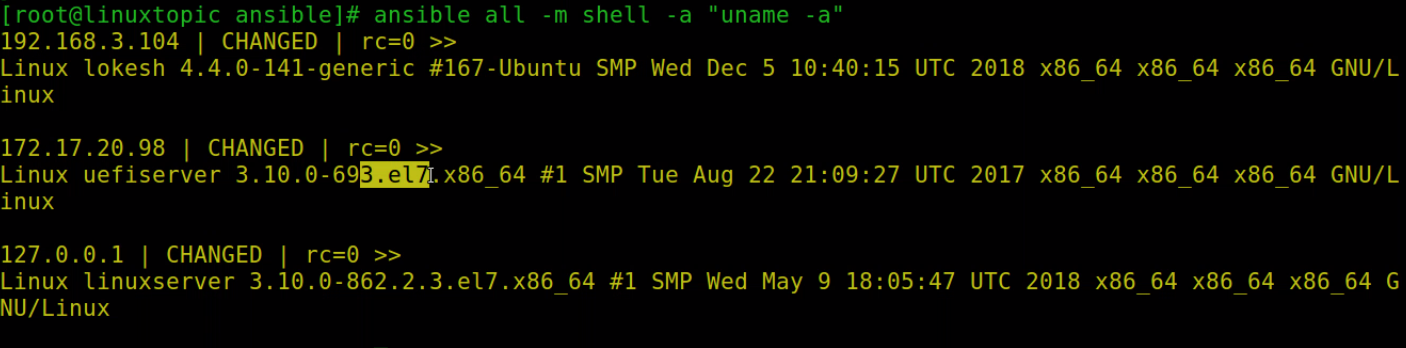
To check kernel version of all hosts using shell module
SSH Port = 22022
User = root
Node 2 :
Ubuntu Server = 192.168.3.104
SSH Port = 22
User = lokesh
User = lokesh
Add remote hosts in inventory
1) Password Authentication
2) Preparing SSH Keys
3) ssh-copy-id
Video Tutorial in Hindi
1) Add remote hosts in inventory using Password authentication
# Add host with password
192.168.3.104 ansible_ssh_user=lokesh ansible_ssh_pass=server32

To Ping Remote hosts group
vi /etc/ansible/hosts[remote]
# Add host with password
192.168.3.104 ansible_ssh_user=lokesh ansible_ssh_pass=server32
To Ping Remote hosts group
ansible remote -m ping
ansible all -m ping
To check all configure hosts
ansible --list-hosts all
To check groups hosts
ansible --list-hosts remote
2) Authentication ansible hosts using ssh key
Prepare ssh key in remote hosts, for example we have Ubuntu 16 with details:
Remote Host: 192.168.3.104
User: lokesh
To Install Openssh-server in Remote host
apt install openssh-server
To generate ssh key using ssh-keygen
ssh-keygenEnter passphrase ( emply for no passphrase) :Enter same passphrase again :
To verify ssh key file
cd .ssh/
cat id_rsa.pub
To create authorized_keys file and copy public key
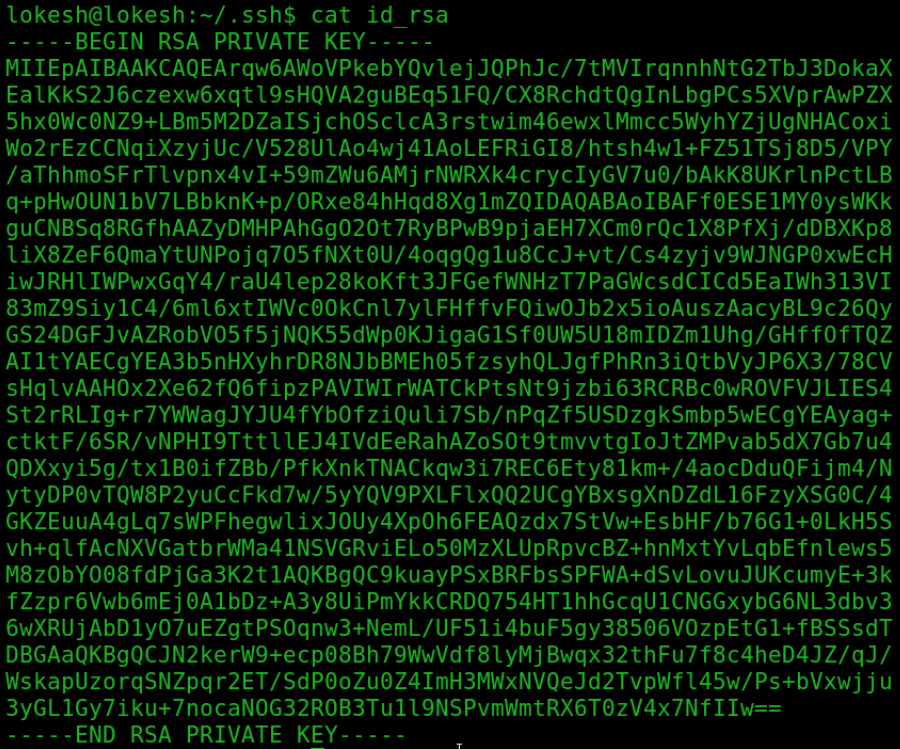
cat id_rsa.pub >> /home/lokesh/.ssh/authorized_keys
cat id_rsa
Note: we require this private key ( id_rsa ) to authenticate with ansible
Login in Ansible Server and create a key file with any suitable name and paste remote hosts Private key ( id_rsa )
vi /etc/ansible/remote-104.key
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEArqw6AWoVPkebYQvlejJQPhJc/7tMVIrqnnhNtG2TbJ3DokaX
EalKkS2J6czexw6xqtl9sHQVA2guBEq51FQ/CX8RchdtQgInLbgPCs5XVprAwPZX
5hx0Wc0NZ9+LBm5M2DZaISjchOSclcA3rstwim46ewxlMmcc5WyhYZjUgNHACoxi
Wo2rEzCCNqiXzyjUc/V528UlAo4wj41AoLEFRiGI8/htsh4w1+FZ51TSj8D5/VPY
/aThhmoSFrTlvpnx4vI+59mZWu6AMjrNWRXk4crycIyGV7u0/bAkK8UKrlnPctLB
q+pHwOUN1bV7LBbknK+p/ORxe84hHqd8Xg1mZQIDAQABAoIBAFf0ESE1MY0ysWKk
guCNBSq8RGfhAAZyDMHPAhGgO2Ot7RyBPwB9pjaEH7XCm0rQc1X8PfXj/dDBXKp8
liX8ZeF6QmaYtUNPojq7O5fNXt0U/4oqgQg1u8CcJ+vt/Cs4zyjv9WJNGP0xwEcH
iwJRHlIWPwxGqY4/raU4lep28koKft3JFGefWNHzT7PaGWcsdCICd5EaIWh313VI
83mZ9Siy1C4/6ml6xtIWVc0OkCnl7ylFHffvFQiwOJb2x5ioAuszAacyBL9c26Qy
GS24DGFJvAZRobVO5f5jNQK55dWp0KJigaG1Sf0UW5U18mIDZm1Uhg/GHffOfTQZ
AI1tYAECgYEA3b5nHXyhrDR8NJbBMEh05fzsyhQLJgfPhRn3iQtbVyJP6X3/78CV
sHqlvAAHOx2Xe62fQ6fipzPAVIWIrWATCkPtsNt9jzbi63RCRBc0wROVFVJLIES4
St2rRLIg+r7YWWagJYJU4fYbOfziQuli7Sb/nPqZf5USDzgkSmbp5wECgYEAyag+
ctktF/6SR/vNPHI9TttllEJ4IVdEeRahAZoSOt9tmvvtgIoJtZMPvab5dX7Gb7u4
QDXxyi5g/tx1B0ifZBb/PfkXnkTNACkqw3i7REC6Ety81km+/4aocDduQFijm4/N
ytyDP0vTQW8P2yuCcFkd7w/5yYQV9PXLFlxQQ2UCgYBxsgXnDZdL16FzyXSG0C/4
GKZEuuA4gLq7sWPFhegwlixJOUy4XpOh6FEAQzdx7StVw+EsbHF/b76G1+0LkH5S
vh+qlfAcNXVGatbrWMa41NSVGRviELo50MzXLUpRpvcBZ+hnMxtYvLqbEfnlews5
M8zObYO08fdPjGa3K2t1AQKBgQC9kuayPSxBRFbsSPFWA+dSvLovuJUKcumyE+3k
fZzpr6Vwb6mEj0A1bDz+A3y8UiPmYkkCRDQ754HT1hhGcqU1CNGGxybG6NL3dbv3
6wXRUjAbD1yO7uEZgtPSOqnw3+NemL/UF51i4buF5gy38506VOzpEtG1+fBSSsdT
DBGAaQKBgQCJN2kerW9+ecp08Bh79WwVdf8lyMjBwqx32thFu7f8c4heD4JZ/qJ/
WskapUzorqSNZpqr2ET/SdP0oZu0Z4ImH3MWxNVQeJd2TvpWfl45w/Ps+bVxwjju
3yGL1Gy7iku+7nocaNOG32ROB3Tu1l9NSPvmWmtRX6T0zV4x7NfIIw==
-----END RSA PRIVATE KEY-----
To set permission
MIIEpAIBAAKCAQEArqw6AWoVPkebYQvlejJQPhJc/7tMVIrqnnhNtG2TbJ3DokaX
EalKkS2J6czexw6xqtl9sHQVA2guBEq51FQ/CX8RchdtQgInLbgPCs5XVprAwPZX
5hx0Wc0NZ9+LBm5M2DZaISjchOSclcA3rstwim46ewxlMmcc5WyhYZjUgNHACoxi
Wo2rEzCCNqiXzyjUc/V528UlAo4wj41AoLEFRiGI8/htsh4w1+FZ51TSj8D5/VPY
/aThhmoSFrTlvpnx4vI+59mZWu6AMjrNWRXk4crycIyGV7u0/bAkK8UKrlnPctLB
q+pHwOUN1bV7LBbknK+p/ORxe84hHqd8Xg1mZQIDAQABAoIBAFf0ESE1MY0ysWKk
guCNBSq8RGfhAAZyDMHPAhGgO2Ot7RyBPwB9pjaEH7XCm0rQc1X8PfXj/dDBXKp8
liX8ZeF6QmaYtUNPojq7O5fNXt0U/4oqgQg1u8CcJ+vt/Cs4zyjv9WJNGP0xwEcH
iwJRHlIWPwxGqY4/raU4lep28koKft3JFGefWNHzT7PaGWcsdCICd5EaIWh313VI
83mZ9Siy1C4/6ml6xtIWVc0OkCnl7ylFHffvFQiwOJb2x5ioAuszAacyBL9c26Qy
GS24DGFJvAZRobVO5f5jNQK55dWp0KJigaG1Sf0UW5U18mIDZm1Uhg/GHffOfTQZ
AI1tYAECgYEA3b5nHXyhrDR8NJbBMEh05fzsyhQLJgfPhRn3iQtbVyJP6X3/78CV
sHqlvAAHOx2Xe62fQ6fipzPAVIWIrWATCkPtsNt9jzbi63RCRBc0wROVFVJLIES4
St2rRLIg+r7YWWagJYJU4fYbOfziQuli7Sb/nPqZf5USDzgkSmbp5wECgYEAyag+
ctktF/6SR/vNPHI9TttllEJ4IVdEeRahAZoSOt9tmvvtgIoJtZMPvab5dX7Gb7u4
QDXxyi5g/tx1B0ifZBb/PfkXnkTNACkqw3i7REC6Ety81km+/4aocDduQFijm4/N
ytyDP0vTQW8P2yuCcFkd7w/5yYQV9PXLFlxQQ2UCgYBxsgXnDZdL16FzyXSG0C/4
GKZEuuA4gLq7sWPFhegwlixJOUy4XpOh6FEAQzdx7StVw+EsbHF/b76G1+0LkH5S
vh+qlfAcNXVGatbrWMa41NSVGRviELo50MzXLUpRpvcBZ+hnMxtYvLqbEfnlews5
M8zObYO08fdPjGa3K2t1AQKBgQC9kuayPSxBRFbsSPFWA+dSvLovuJUKcumyE+3k
fZzpr6Vwb6mEj0A1bDz+A3y8UiPmYkkCRDQ754HT1hhGcqU1CNGGxybG6NL3dbv3
6wXRUjAbD1yO7uEZgtPSOqnw3+NemL/UF51i4buF5gy38506VOzpEtG1+fBSSsdT
DBGAaQKBgQCJN2kerW9+ecp08Bh79WwVdf8lyMjBwqx32thFu7f8c4heD4JZ/qJ/
WskapUzorqSNZpqr2ET/SdP0oZu0Z4ImH3MWxNVQeJd2TvpWfl45w/Ps+bVxwjju
3yGL1Gy7iku+7nocaNOG32ROB3Tu1l9NSPvmWmtRX6T0zV4x7NfIIw==
-----END RSA PRIVATE KEY-----
To set permission
chmod 600 /etc/ansible/remote-104.keyTo login on remote host by ssh key
ssh -p22 -i /etc/ansible/remote-104.key [email protected]
Add remote host in inventory file using key file path
vi /etc/ansible/hosts[localhost]
127.0.0.1
[remote]
192.168.3.104 ansible_ssh_user=lokesh ansible_ssh_private_key_file=/etc/ansible/remote-104.key
Verify hosts connectivity using ping module
ansible remote -m ping
ansible all -m ping
3) ssh-copy-id
To copy ssh key using ssh-copy-id command
ssh-copy-id -p22 [email protected]Type current password of lokesh user, it will auto copy the ssh key
Here: ssh-copy-id is command, -p22 is ssh port, lokesh is ssh user and 192.168.3.104 remote host
Host 2:
ssh-copy-id -p22022 [email protected]
Add Remote hosts in Inventory file
vi /etc/ansible/hosts[localhost]
127.0.0.1
[remote]
192.168.3.104 ansible_ssh_user=lokesh ansible_become_pass=server32
172.17.20.98 ansible_port=22022
In inventory we use ansible_become_pass=server32, means we give sudo privileges
To verify all hosts using ping ad-hoc command
ansible all -m ping
To check kernel version of all hosts using shell module
ansible all -m shell -a "uname -a"


